Spheres of Identity
This is a mirror of an article originally published on newdesigncongress.org. It has been slightly edited to fix the markup for this site.

1Conceptualisation and governance are not the only aspects shaping the use and outcomes of digital identity systems. The topologies of digital identity, and their very observation, are additional dimensions that affect these socio-political structures. Existing research into digital identity management systems describe four such topological models —“siloed,” “centralised,” “federated” and “user-centric” — and these models can be used to trace how topologies enable specific relationships between users, identity providers and service providers. The models of digital identity offer methods for identifying deterministic points of control, risk, custodianship and opportunity within any specific identity system. Each configuration has specific strengths and vulnerabilities, as well as contrasting implications for complexity, economic sustainability and sovereignty. To understand digital identity at a macro level is to evaluate the implementation of historical digital identity systems, or the potential of emergent or proposed new systems through these models. This contributes to an important materialist analysis of the entanglement of rhetoric and reality within complex systems at scale.
While the four models of digital identity offer useful terminology to codify digital identity topologies, they are also frustratingly contradictory. Each model contains limitations that affect how we observe and evaluate digital identity. No matter how carefully a digital identity is designed, in practice digital identity resists classification into these neat categories. This research note examines the blurry boundaries between models that intend to define a given identity system, but remain contingent on and influenced by use, legal circumstances, perspective and technological developments. We apply our working definition2 of digital identity and interrogate these models alongside our earlier two3 problem statements4 that define this research. This approach allows us to shed new light on contradictions, attack surfaces, complexity, opportunity and other dynamics shared across each of the four models to set a foundation for our future case studies and intervention work.
Scholarship on digital identity management systems help us delineate the distinct properties of the aforementioned topologies. In Digital Identity Management5, authors Laurent-Maknavicius & Bouzefrane introduce the concepts of users, identity providers (IdP) and service providers (SP) to unify the terminology around distinct Digital Identity Management systems:
“– a user: a natural person with at least one digital identity wishes to conduct a transaction;
– an identity provider (IdP): an entity in charge of digital identity management and of the execution of the authentication mechanism. It enrolls any new user by registering their identifier(s) and some of their attributes. During enrollment, according to its policy, it may be necessary to verify the veracity of the identity provided with the help of an identity card, proof of residence, or even mere proof of receipt of an email;
– a service provider (SP): an entity providing users with a service usually a Web service, and relying on the IdP in order to verify the identity given by the user.”
Using these three actor types, Laurent-Maknavicius & Bouzefrane describe four typical models—the siloed model, the centralised model, the federated model and the user-centric model.
The siloed identity model
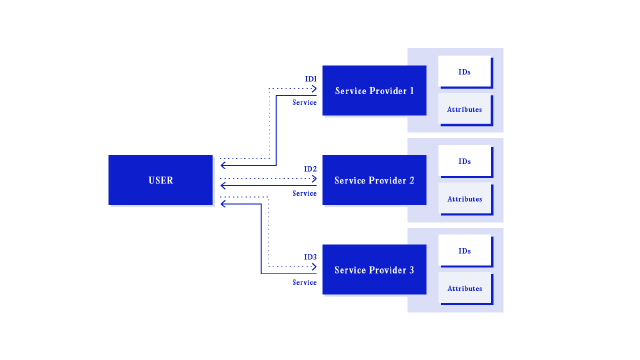
When a service provides an identity to a user, and this identity is encapsulated to interactions between the two parties only, this is an example of a siloed identity model. The siloed identity is arguably the most familiar to users—a ubiquitous example might be an online store requiring user accounts for customers to make purchases, track orders or contact customer support.
Central to understanding the siloed identity model is its two key characteristics: the service provider is also the identity provider, and the service handles all the authentication and authorisation for the identity. The user creates a new identity for each service they wish to interact with. Each service provider is a different digital identity provider carrying distinct attributes that depend on their specific goals.
User-facing siloed identities usually have well-established user experience flows structured around the creation of a user account, typically via an email address and password. Validation and management of the new account is handled via communication to the user’s supplied email address. The tight scope of a siloed identity means a single account is relatively easy for a user to setup and maintain, as their lack of portability or interoperability spares users from the complex privacy or security implications inherent in identity reuse across multiple service providers. For providers, siloed identities are often initially low cost and incredibly easy to implement; their design patterns are amongst the first things learned by systems designers, user experience practitioners and engineers.
The centralised identity model
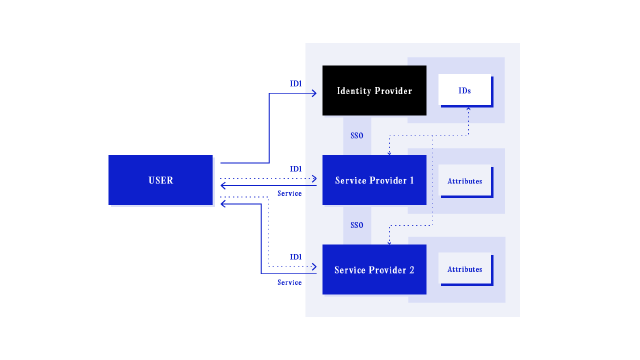
When a digital identity provided by one provider is integrated into the system of an unrelated service provider, this is a centralised identity. In this model, the identity provider handles all aspects of design, authorisation and authentication, and provides methods of integration for external service providers. With a single credential pair, users access different service providers in the system and are represented by the same identity across each platform. This is referred to as Single-Sign On.
Regardless of how a centralised identity comes into existence, the identity provider is always externalised from the the service provider. In all other models, the responsibility for the identity lies partially or wholly with the service provider, or in decentralised cases, the user. In a centralised model, the identity provider is responsible for the design and operation of all authorisation and authentication completed with the identity. This dynamic creates a particular centre of power, where the identity provider becomes a gatekeeper for the access and governance of the identity system over time.
Microsoft Passport8 is an historical example of a centralised identity. Here, Microsoft leveraged the characteristics of centralised identity in an attempt to position itself as the singular identity provider for the web. The project failed to gain traction due in part because of suspicion towards Microsoft’s motives9 and the outsized power such a system would help an already powerful company accumulate more influence. Microsoft’s efforts with Passport led to further theorisation of digital identity systems by Kim Cameron, who in “Laws of Identity”, suggested that an identity system would have to accommodate a pluralism of operators and technologies to gain traction10. This, in turn, led to the development of the federated digital identity model.
The federated identity model
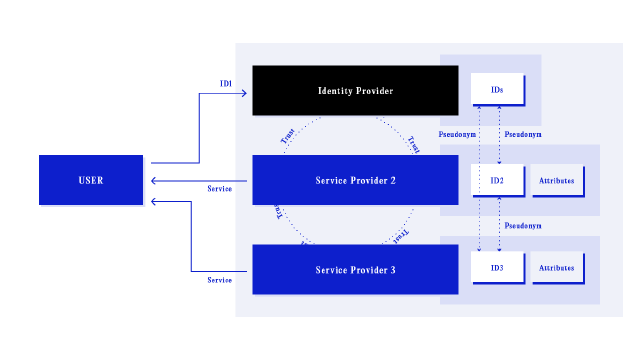
When an identity provider is separated from the service provider, but the identity is an interoperable component or protocol within a wider ecosystem, this is a federated model of digital identity. In addition, the federated identity model allows for data exchange across administrative boundaries. Systems that have implemented federated identities allow services outside of an organization’s control to authenticate against the organisation’s identity provider, given that they meet specific criteria. These conditionals—known as the circle of trust12—are a key component of federated identity. They require all parties to rely on asserted claims about a digital identity as conveyed by the identity provider within the context of the protocol. The circle of trust can be defined and enforced by legislation, cryptography, consensus or technological platform, and the negotiated outcome allows individual identity providers to provide standardised credentials that can be validated by other identity providers or service providers. The federated identity model attempts to balance a higher degree of control and usability inherent to centralised identity providers against a decentralisation of absolute authority over the final design of the identity13.
Service providers rely on shared consensus to trust the authentication assertions of the identity provider, and the identity provider trusts the service provider to handle the provided user information with care. Kylau et al. describe that “trust relationships are usually established by a set of contracts defining obligations and rights each party has and policies each member has to follow” and that setting up such contracts involve “huge effort”14.
However, using specific protocols for federated identity management makes this substantially easier because the contours of trust relationships are established and defined by these protocols. Since the early 2000s, several successful and widely used examples of federated identity exist, including Security Assertion Markup Language (SAML), OpenID 1.0 for authentication, and Open Authentication (OAuth) for authentication.
Federated identity management systems built upon these protocols provide standardised and “unified set[s] of policies and procedures allowing identity management information to be transportable from one security domain to another.”15 Users can login to an on-line store using the federated identity of a large and well-recognised platform — “Login with [Google|Facebook|Microsoft]”— rather than completing the steps necessary to create a new identity and this user experience implies a shared single identity. While this may be true in some implementations, the online store is just as likely to implement its own siloed identity under the hood for the user (described as the Pseudonym in the figure above) and authenticate that against the federated identity provider.
Federated identities have no central authority, and anyone can set up an identity provider or implement federated identities into a service provider17. Federated identities exist both as a commercial services (Okta, Yubikey, Microsoft Azure) and self-hostable white-label technologies that can be implemented in a new or existing application (Keycloak, Authentik). Finally, federated identity models allow Service Providers to configure multiple identity providers, broadening the likelihood that a user have a pre-existing account with one of several authentication options offered. Depending on the which federated identity the user elects to use, this can have wildly unpredictable data privacy implications, as users are forced to trust service providers to respect their privacy as they receive and process an offered identity credential18.
The user-centric identity model
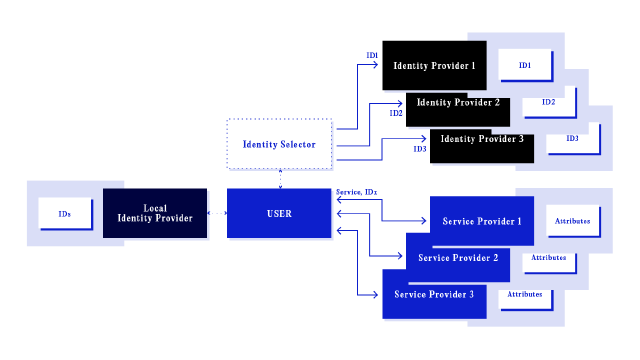
When a digital identity is derived entirely from the user, or the user also acts as the identity provider, this is considered a user-centric digital identity model. This approach often — but not always — emphasises user autonomy and contrasts with traditional identity management systems, where control is typically centralised with service providers or institutions. For Laurent-Maknavicius et al., the key aspects of a user-centric identity include user-led control, attribute compartmentalisation (framed as privacy protection), interoperability, and full decentralisation20.
In one common example of user-centric identity, a user actively develops and manages their identity attributes through a local identity provider, selectively disclosing information to various service providers based on their preferences and the specific context of each interaction. In practice, several protocols, such as OpenID 2.0 and OpenID Connect, have been developed to facilitate this process. These protocols combine authentication and authorisation, allowing users to authenticate across administrative boundaries while disclosing only a limited amount of identity attributes, such as a profile picture and email address.
Performative identity is another example of user-centric digital identity, where an identity is enacted or performed through user actions and interactions. In this case, users deploy context-specific personas and engage in active compartmentalisation of their identity when interacting with other users or service providers.
Finally, user-centric identity can also be derived from user characteristics, where individual user behaviour, physical characteristics, or digital footprints become aspects in assembling a unique and recognisable identity. Here, the implied user empowerment inherent to user-centric digital identity is inverted despite the model adhering to the conditions of the model at a surface level.
From Models to “Spheres”
In Identifying and Defining the Digital Self21 and Self-(De)termination: The Fatal Ambiguity of Digital Identity22, we examine systemic flaws in the conceptualisation and administration of digital identity and their broader societal consequences. The practice of modelling and evaluating digital identity contain similar shortcomings that contribute to the weakening of digital identity. At its core is a key flaw: the evaluation model(s) for a digital identity shifts over time, based on the observer’s motivations, perspective, and beliefs. The amorphous nature of applied digital identity models conflicts with the rigid requirements of evaluation. Multiple contradictory frameworks can be employed simultaneously to a single digital identity system, creating blurred boundaries and tensions between theoretical frameworks and practical implementations23.
This realisation that identity models can overlap and coexist necessitates a new language and approach to digital identity management. This is a situation that is aggravated as best-practices and historical decisions are layered on top of each other. To address these issues, we propose the concept of -spheres of identity_, which accommodates a more flexible and adaptive approach to identity evaluation, moving beyond the rigidity of today’s best practice.
The trade-offs of the siloed identity model best exemplify these issues. As the oldest and most widespread model, siloed identity is defined by the fact that all facets of control, custodianship, governance and responsibility is solely held by the dual identity/service capabilities of the provider24. This model is particularly suitable for representing non-human entities or implementing application-specific attributes and identifiers, allowing systems designers to model and plan interactions with computers and processes according to specific protocols or behaviours. However, managing multiple isolated identities can become an unreasonable challenge, especially for infrequent services such as annual tax reporting or occasional online shopping25.
Users are often asked to use their email address as their unique identifier, creating a subtle but important cognitive link between discrete, non-interoperable siloed identities. To manage the complexity of an ever-increasing repository of siloed identities, users frequently resort to password reuse, which decreases the complexity of identity management for themselves. The reuse of credentials can thus be understood as a form of DIY portability deployed to mitigate the core limitations of the non-portable properties of the siloed identity model. Ethnographic work on sociotechnical systems has extensively documented the way people use and need “work-arounds,”26 kludges27, and other patches to be able to make effective use of systems, and this DIY portability is an example of this work.
User-driven DIY-portability has major consequences. When compromised, DIY-portable credentials also become DIY-portable tools for attackers. Credential reuse in siloed identities is now a major attack surface for cybercrime; a large-scale data breach of one provider’s identity system unlocks cascading access to other providers, and the user must respond individually to each instance of credential reuse. Where siloed identities lack interoperability and do not share global namespaces between identity/service providers, the ‘user-led’ soft-patch creates an ad-hoc global namespace that allows attackers to traverse multiple isolated platforms, testing credentials and compromising these unrelated identities28. Thus, a theoretically siloed model in practice becomes centralised and portable over time.
An ad-hoc alternative to credential reuse is the use of password managers, where a user self-manages a single master identity that grants access to a secure personal database containing all other credentials. When practised with a high degree of discipline, this method allows for the use of unique usernames and randomly generated passwords that user does not have to remember. In the case of a data breach, the cascading access to other providers through credential reuse or DIY portability does not occur29. At the same time, the user must only commit a limited number of credentials to memory. In such a scenario, theoretically siloed identities remain siloed in practice, but ‘soft-managed’ by an external centralised identity — the password manager.
Despite the security risks associated with ad-hoc portability, the siloed identity model offers significant advantages for user agency, ‘consent’30 and privacy. Its encapsulated nature allows users to deliberately create performative identities in order to share only aspects of their identity or assume others, or maintain a form of defensive control over—and compartmentalisation of—the identity creating identity personas to minimise spam and defend against profiling. For instance, users might create temporary e-mail addresses or disposable identities for activities such as exploring sexual, gender, and other marginalised aspects of identity or engaging in political debate, as well as avoiding unsolicited marketing material. The siloed identity model allows users to compartmentalise identity attributes to different services, exposing only the minimally required amount to get access to a particular service. This is especially the case in combination with the use of password managers and temporary e-mail addresses. By compartmentalising identity attributes, users can expose only the minimally required information to access specific services, aligning the siloed model with user-centred identity principles.
Performative user-centric identities can be user-driven statements of self-curation and representation in a digital system. A digital manifestation of Erving Goffman’s “identity performance” concept, this model draws from the idea that identity is not a fixed attribute but a performance that can vary across different contexts31. In digital environments, users actively construct and manage their identities to suit specific interactions, audiences, and purposes. Pseudonyms, digital avatars, and digitally-derived real world pseudo-identities (such as fursonas32) are all examples of performative identity.
In some ways, identity personas share conceptual motivations with performative identity. But whereas the performative is driven by play or a desire to project oneself into the digital world, personas emerge when users strategically compartmentalise their identity as a form of defensive security33. Identity personas allow individuals to create multiple, distinct personas for various online interactions, thereby limiting the exposure of personal information and reducing the risk of identity-related threats. Each persona can be tailored to specific contexts, such as professional networking, social media, or online shopping, ensuring that only relevant information is shared with each service provider. In this way, users exert a level of control over data leakage across multitudes of service providers. These strategies can be employed across a number of identity models, but can fall apart when used on top of a centralised identity34.
The use of multi-factor authentication (MFA) has emerged as an additional layer of defence to address some of the downsides of the siloed identity model. There are a variety of MFA implementations, including physical hardware keys, application-based TOTP (like Authy, FreeOTP, and Google Authenticator), SMS codes sent to a user-nominated phone number, user-supplied biometric scans, or linking the siloed identity to an out-of-band centralised identity. Regardless of the method, the goal of MFA is to validate user ownership of an identity by proving access to another, introducing enough friction to disincentivise an attacker while remaining user friendly.
MFA is a challenge that further complicates the siloed digital identity, as different implementations establish various dependencies and “soft-links” between identities. For example, an SMS-based MFA is tied to a phone number, and this is an example of a centralised identity. Similarly, a hardware MFA key may be derived from a federated protocol. These “soft-links” create intentional barriers of access for the siloed identity, and once introduced, cannot be conceptually separated. The identity model of the “soft-linked” MFA influences the relationships between the user, identity providers and service providers.
Service providers often struggle to distinguish genuine human siloed identities from automated equivalents that are often adversarial35. As a result, many services incorporate steps that provide rudimentary ad-hoc ‘proof-of-personhood’. These measures, such as highly inaccessible CAPTCHAs36 or device sensor surveillance37, aim to verify human presence but can also lead to the creation of shadow identities sold to data brokers38. In these cases, are the automatically generated profile or the credentials used to access a service the actual identity in use? The answer is often unclear.
Beyond proof-of-personhood, service providers that rely on siloed identities often work from a one user, one account design that assumes the digital identity represents a single individual39. In practice, service providers are almost always unable to determine whether one user has multiple accounts or whether multiple users are using one account. While tying a specific person/user to each account may be required for some services and specific industries, such as banking and telecommunications that must adhere to Know Your Customer (KYC) regulations for legal and regulatory reasons, this does not ensure the accuracy of attestation of identity that many assume. Shared siloed identities can also have serious implications: the actions of one individual using a shared account may have platform-based or real world consequences for another individual who is legally bound to the digital identity. A 2024 exposé on automated identification and targeting systems used by the Israeli military underscores how the “one user one account” paradigm has disastrous outcomes for those wrongly identified. Speaking to +972 Magazine, a source familiar with these operations describes the consequences of this: “In war, Palestinians change phones all the time. […] People lose contact with their families, give their phone to a friend or a wife, maybe lose it. There is no way to rely 100 percent on the automatic mechanism that determines which [phone] number belongs to whom.”40
The blurred boundaries and simultaneous applicability of different identity models extend beyond the siloed model to centralised and federated models. The key differentiator of the centralised model was the separation of identity provider from service provider. In the federated model the identity provider can be used across administrative domains allowing to separate organisations and still interoperate.
Historically, the centralised and federated models were distinct, but modern identity management software has blurred these differences over time. Federated identity systems are implemented in universities or other large organisations as a single credential, providing a variety of in-house or external resources to users. In some cases, external authentication for proof of graduation or employment. The ability to link multiple services together via a single user authentication flow is known as “Single Sign-On” (SSO), where a user supplies a single set of credentials (usually username/password, sometimes with multi-factor authentication) to authenticates against different services. Federated identity systems such as, OpenID, OAuth, OpenID Connect, establish a “Circle of Trust” through technical means rather than organisational agreements to allow for Single Sign-On. At the same time, they can make a federated digital identity indistinguishable from a centralised identity. To complicate matters more, later versions of OpenID and OpenID Connect were designed to be user-centric systems, but are often implemented in centralised or federated fashions.
A key property of the federated model is that credentials remain with the identity provider, with only necessary attributes shared with the service provider. This theoretically enhances the privacy of the identity system, compared to centralised or siloed identities entrusted to third party identity providers. Users benefit from using limited number of identity providers to access a larger amount of service providers. However, in practice, the difference between identity provider and service provider is not as strict as the theoretical models make it appear. The examples of “Login with Google” and “Login with Facebook” demonstrate how identity providers can simultaneously be service providers who specifically base their mode of operation user data surveillance. This can have consequences for the user’s privacy, as these identity providers can gain insights about a user’s behaviour they would otherwise not have, would the user not use that identity provider as a login mechanism. This dynamic is not fully captured in theoretical models.
Furthermore, the relationship between dual identity/service providers and federated identity providers tends to be uni-directional. While users can use Google as an identity provider for a local online store, the reverse is not typically possible. This asymmetry highlights the need for a more nuanced understanding of identity models, recognising the evolving interplay between centralised, federated, and siloed systems.
Because these dynamics remain unaddressed, digital identity systems in the consumer internet space have consolidated in to a handful of providers such as Google or Facebook41. This is aggravated by the so-called “NASCAR problem”, named after the many corporate logos that adorn sponsored racing cars. Here, a service provider’s login or sign up interface features a gallery of logos, each representing different compatible identity providers to authenticate with. Like the shortcuts of credential reuse in siloed identity, users take shortcuts to reduce complexity. The amount of choice leads people to and opt to pick familiar or recognisable brands42. As a result, large commercial technology providers have seized on user behaviour to become global centralised digital identity providers.
As federated models centralise, centralised models federate. The widespread deployment of state-backed national e-ID schemes in Northern Europe provide good examples of centralised identities that become interoperable across organisational boundaries. In Sweden, BankID operates as a “platform of platforms,”43 offering both proof-of-personhood and centralised digital identity management via API endpoints and legislation. Administered by a single corporate entity owned by Sweden’s largest banks, BankID’s proof-of-personhood is backed by each bank’s KYC procedures, which in turn relies on government identity systems. BankID is used to authenticate against a wide variety of both public and private service providers, ranging from payment providers to insurers to the tax office and the social welfare system44.
Understanding these dynamics in terms of spheres rather than as rigid models is unconventional, but allows for seemingly counter-intuitive—yet justified—claims when evaluating digital identity. Hence, the following examples of topologically diverse systems can still be considered to belong to the centralised sphere:
- Identities embedded in hardware tokens or access cards, such as Yubikey’s multi-factor authentication keys or HID Global’s suite of products, including employee identification cards that provide building access, and government-issued biometric passports;
- ‘Tunnelled identities,’ where the identity is embedded in open source connection security protocols, such as OpenVPN or Wireguard. Examples include Tailscale, where the centralised identity is cocooned within a secure virtual network connection and integrated into a service provider;
- Blockchain/Web3 identities, where the user identity is tied to a token or other value store, and the identity is considered portable via a common underlying protocol (such as Ethereum), or via conduction transactions between two parties to move the identity between implementations45;
- Identities based on messaging protocols, where the identity is returned after an automated system makes contact with a user via a messaging platform with a one-time code and the user completes a sign in or sign up process using that code. These are niche but rapidly expanding, such as Telegram’s third party authentication system or services that advertise ‘passwordless’ sign up by providing authentication links via email, or;
- Identities derived from existing standardised SSO implementations—usually OAuth, LDAP or OpenID Connect—that operate only as an identity provider. For example, the Berlin BVG public transportation company manages its passenger accounts and ticketing with the assistance of an identity primitive derived from the Keycloak open source project46, and has a degree of interoperability with other public transport, taxi services and rideshare providers within Germany. Other examples include Okta’s Identity Cloud and the open source Authentik project.
Research on digital identity management systems has identified several models—“siloed,” “centralised,” “federated,” and “user-centric”—each with distinct properties and a historically progressive trajectory. Each model builds on, and improves, the shortcomings of its predecessors. However, in practice, the clear delineations of these ideal-typical forms blur, contributing to the discrepancies when trying to reckon with the failings of digital identity systems.
To address these discrepancies, we propose shifting from rigid identity management models to an approach that accommodates the amorphous nature of digital identity. This means observing and describing topologies as they truly are, rather than as they are purported to be, and developing methods that allow for discrepancy or contradiction at a fundamental level. As we witness a widespread push for novel identity systems that aim to address the perceived shortcomings of earlier generations, this reconsideration becomes particularly pertinent. It is essential to question whether older generations of identity systems allowed for more flexibility and whether newer systems genuinely overcome the limitations of their predecessors.
We challenge the topological determinism often found in technical communities—both builders and critics of technology. Conceptualising a particular identity system as fitting a specific topological model obscures attack vectors and vulnerabilities typically associated with other models. To adopt a more fluid approach to identity evaluation is to make sense of the complex and messy terrain of digital identity systems. This is an inescapable requirement for rethinking the first principles of digital identity if we are to implement resilient representations in uncertain and unstable digitised societies.
Roel Roscam Abbing
Cade Diehm
Benjamin Royer
August 2024
-
This Research Note is an abridged chapter of our forthcoming Digital Identity research report. ↩︎
-
The six properties of our working definition for digital identity are: Serialisation, Custodianship, Presentation, Authentication, Authorisation and Assetisation. See more in the relevant chapter of Identifying and Defining the Digital Self. ↩︎
-
Identifying and Defining the Digital Self
25 January 2024 ↩︎ -
Self-(De)termination: The Fatal Ambiguity of Digital Identity
05 March 2024 ↩︎ -
Digital Identity Management
Maryline Laurent-Maknavicius, Samia Bouzefrane, et. al., ISTE Press
2015 ↩︎ -
A schematic representation of the siloed identity model.
Digital Identity Management
Maryline Laurent-Maknavicius, Samia Bouzefrane, et. al., ISTE Press
2015 ↩︎ -
A schematic representation of the centralised identity model.
Digital Identity Management
Maryline Laurent-Maknavicius, Samia Bouzefrane, et. al., ISTE Press
2015 ↩︎ -
See the Microsoft Account History chapter in Wikipedia for additional context. ↩︎
-
Heading MS Off at the Passport
Declan McCullagh, Wired Magazine
August 2001 ↩︎ -
The Laws of Identity
Kim Cameron, Microsoft Corporation
May 2005 ↩︎ -
A schematic representation of the federated identity model.
Digital Identity Management
Maryline Laurent-Maknavicius, Samia Bouzefrane, et. al., ISTE Press
2015 ↩︎ -
Liberty Alliance Outlines Legal Framework for Circles of Trust to Comply with European Union Data Protection and Privacy Laws
Liberty Alliance
12 April 2005 ↩︎ -
Federated Identity Management
David W. Chadwick, Foundations of Security Analysis and Design V: FOSAD
2009 ↩︎ -
Trust Requirements in Identity Federation Topologies
Uwe Kylau et al., International Conference on Advanced Information Networking and Applications
2009 ↩︎ -
Securing Digital Identities in the Cloud by Selecting an Apposite Federated Identity Management from SAML, OAuth and OpenID Connect
Nitin Naik & Paul Jenkins, 11th International Conference on Research Challenges in Information Science
2017 ↩︎ -
A screenshot of a typical login interface that supports different Federated identity models. Here, six different sign-in options for a web service, each represented by a different company logo (Google, Facebook, Twitter, GitHub, Email, Phone) on corresponding buttons. Each button is styled with the respective brand’s colors, making the interface look busy and potentially confusing for users. This is an example of the NASCAR Problem, described below in, “From Models to Spheres.” ↩︎
-
Oauth and Openid 2.0
Pauli Kaila, Proceedings of the Seminar on Network Security, vol. 18 (From End-To-End to Trust-to-Trust ↩︎ -
Digital Identity Management
Maryline Laurent-Maknavicius, Samia Bouzefrane, et. al., ISTE Press
2015 ↩︎ -
A schematic representation of the user-centric identity model.
Digital Identity Management
Maryline Laurent-Maknavicius, Samia Bouzefrane, et. al., ISTE Press
2015 ↩︎ -
Digital Identity Management
Maryline Laurent-Maknavicius, Samia Bouzefrane, et. al., ISTE Press
2015 ↩︎ -
Self-(De)termination: The Fatal Ambiguity of Digital Identity ↩︎
-
The Identity Crisis Security, Privacy and Usability Issues in Identity Management
Gergely Alpár, Jaap-Henk Hoepman & Johanneke Siljee, Web of Trust II: ID2020 Design Workshop
2020 ↩︎ -
Digital Identity Management
Maryline Laurent-Maknavicius, Samia Bouzefrane, et. al., ISTE Press
2015 ↩︎ -
The Domains of Identity a Framework for Understanding Identity Systems in Contemporary Society
Kaliya Young, Anthem Press Ethics of Personal Data Collection Series
2020 ↩︎ -
In the Age of the Smart Machine: The Future of Work and Power ↩︎
-
Work-Arounds, Make-Work, and Kludges
Philip Koopman & Robert R. Hoffman, IEEE Intelligent Systems 18, no. 6
2003 ↩︎ -
Protecting Accounts from Credential Stuffing with Password Breach Alerting
Kurt Thomas et al., 28th USENIX Security Symposium
14-16 August 2019 ↩︎ -
Analysis on the Security and Use of Password Managers
Carlos Luevanos et al., 18th International Conference on Parallel and Distributed Computing, Applications and Technologies
2017 ↩︎ -
Faceted Id/Entity: Managing Representation in a Digital World
danah boyd, Massachusetts Institute of Technology
2002 ↩︎ -
Keeping the Magic: Fursona Identity and Performance in the Furry Fandom
Jakob W Maase, Western Kentucky University
2015 ↩︎ -
Beyond Full Abstraction: Formalizing the Security Guarantees of Low-Level Compartmentalization
Yannis Juglaret et al., ArXiv
14 February 2016 ↩︎ -
An illustrative example of this falling apart is when the “People You May Know” feature launched on Facebook, many performative identities and personas became visibly linked to one another as the system started recommending personas to people who otherwise intended to keep them secret and separate.
See also: ‘People You May Know:’ A Controversial Facebook Feature’s 10-Year History
Kashmir Hill, Gizmodo
8 August 2018 ↩︎ -
The Blue Check of Credibility: Does Account Verification Matter When Evaluating News on Twitter?
Stephanie Edgerly & Emily Vraga, Cyberpsychology, Behavior, and Social Networking 22
8 March 2019 ↩︎ -
Gotta CAPTCHA ’Em All: A Survey of 20 Years of the Human-or-Computer Dilemma
Meriem Guerar et al., ACM Computing Surveys 54, no. 9 8 October 2021 ↩︎ -
Discovering Human Presence Activities with Smartphones Using Nonintrusive Wi-Fi Sniffer Sensors: The Big Data Prospective
Weijun Qin et al., International Journal of Distributed Sensor Networks 2013
1 December 2013 ↩︎ -
Leaking Privacy and Shadow Profiles in Online Social Networks
David Garcia, Science Advances 3, no. 8
4 August 2017 ↩︎ -
The Domains of Identity a Framework for Understanding Identity Systems in Contemporary Society
Kaliya Young, Anthem Press Ethics of Personal Data Collection Series
2020 ↩︎ -
‘Lavender’: The AI Machine Directing Israel’s Bombing Spree in Gaza
Amjad Iraqi, +972 Magazine
3 April 2024 ↩︎ -
Decentralizing the Social Web: Can Blockchains Solve Ten Years of Standardization Failure of the Social Web?
Harry Halpin, Internet Science
2019 ↩︎ -
The NASCAR Problem
IndieWeb Wiki
3 June 2022 ↩︎ -
Digital Identity as a Platform of Platforms: Investigating Bankid’s Effect on Swedish Organizations
Claire Ingram Bogusz & Harris Kyriakou, ECIS 2023: European Conference on Information Systems
11-16 June 2023 ↩︎ -
Achieving Payoffs from an Industry Cloud Ecosystem at BankID
Ben Eaton et al., MIS Quarterly Executive
28 November 2014 ↩︎ -
Consider, for instance, Moxie Marlinspike’s reflections on the platformisation of blockchain systems. ↩︎
-
Although little has been made public about BVG’s use of Keycloak, the source of BVG-Konto login screen shares common code with Keycloak, and it is reasonable to assume this identity implementation is derived from the open source project. ↩︎